Pinterest has been developing computer vision technology since 2014 and is now applying it to visual search queries and ad targeting. Pinterest wants to do for visual search what Google has done for text search. Since assembling a small team…
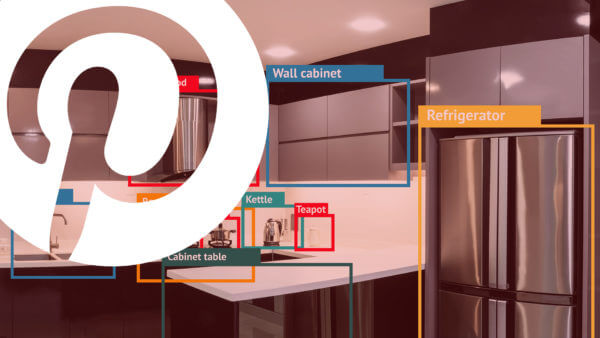

Pinterest has been developing computer vision technology since 2014 and is now applying it to visual search queries and ad targeting. Pinterest wants to do for visual search what Google has done for text search. Since assembling a small team…

Columnist Kevin Rowe shares tips on working with online influencers to boost your brand’s link profile, its brand visibility and traffic to your site. You may be thinking that no one wants to share your content, but the opposite is…

AT&T is addressing one of the biggest challenges to 5G deployment, installing small cell towers on street lights. 5G promises to revolutionize a range of industries, delivering speeds once thought impossible. Unfortunately, the fastest varieties of 5G are limited by…

The FBI is warning athletes to leave their personal devices at home when they travel to Beijing for the Winter Olympics. The Dutch Olympic Committee warned its athletes in mid-December against bringing personal electronics to China. China has a long-standing history of…

Dutch athletes are being warned not to bring their phones and laptops to China for the Beijing Winter Olympics over espionage fears. China has one of the worst reputations in the world for surveillance and espionage, regularly monitoring its own…

Transitioning and migrating your data/business into the cloud is one of the most critical methods of improving your business’s daily operations. A cloud service can streamline operational efficiency, provide better storage/access for data, and much more. But, there are times…

Popular password manager LastPass says master passwords are safe, despite many users believing otherwise. Password managers are important elements in cybersecurity. A good password manager saves the many different passwords users collect, notifies them when one is too easy or…

Storing, organizing, and managing your business’s data is no easy task, yet companies of all sizes and in all industries require this service. Because maintaining your own storage repository would require an immense amount of work and lots of money,…

Remote work and hybrid work environments continue after the move toward these scenarios was sped up by the start of the pandemic in 2020. Some challenges remain, however. According to research, organizations using remote or hybrid work are experiencing cyberattacks…
Zoom’s purchase of Five9, a leading intelligent cloud contact center provider, is undergoing a US national security review. Zoom announced in July that it was purchasing Five9. Zoom has its roots in the enterprise market, before becoming a household name as a…