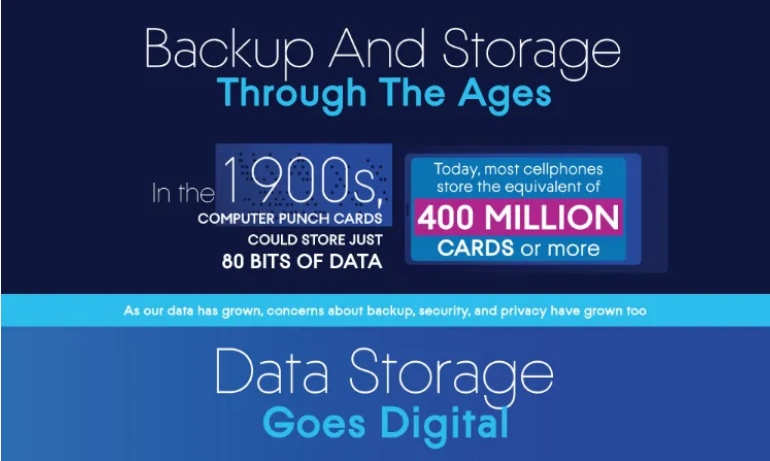
We have been blessed with a boom in technology and what we can do with it. Can you imagine explaining to someone from the 1900s that on a thin little wafer we have libraries of information? The first punch cards could only store 80 bits of data, most cellphones today store the equivalent of 400 million cards or more. As our data has grown, concerns about backup, security, and privacy have grown too.
The History Of Storage
People used to store information on stone or paper, which we still do today. However, in the 1950s we first started storing data digitally. IBM invented RAMAC 305, the first magnetic disk drive. Measuring 16 feet tall and weighing over a ton each drive stored 3.75 MB of data, which means you would need 534 RAMACs just to store Microsoft Office nevermind the memory needed for an operating system.
Magnetic disk drives made random data access possible, the alternative was waiting for a somewhat automatic filing system of drums or tape to reel to the desired data. By the 1960s MDDs became the standard for data storage and backup, leading up to the invention of RAM.
Semiconductor Random Access Memory vastly grew in storage capacity, going from 8 bits per chip to 256. The more chips the more memory, this allowed a progression away from needing huge rooms to store memory. In 1967 memory storage was downscaled even further, with the advent of the floppy disk.
IBM first sold the 8-inch floppy disks in 1971 affording the ability to buy, sell, and share data. In the same year, the first computer virus was invented as an experiment, motivating new developments in security. Not 7 years later, the first hot site was deployed by Sungard Information Systems, safeguarding against potential outages with a backup website.
In the 1980s, the first patented cybersecurity technology in the U.S. was developed at MIT. The Rivest-Shamir-Adleman Algorithm (RSA) is a type of public-key cryptography that formed the basis for data encryption. RSA allowed secure email and other online transactions.
Apple II computers brought 5-¼ inch drives for floppy disks to consumers, as they became more prevalent. Soon after Dr. Popp Ransomware was spread using floppy disks. The first known ransomware locked infected computers and demanded payment for a “software lease.”
In the 1990s, we went back to having huge rooms of computers, but in a good way. Network-Attached Storage (NAS) was a dedicated file-level storage server that used ethernet connections, developed in ‘89 by Auspex Systems.
NAS was made less relevant by Storage Area Networks (SAN), which connected devices and shared data across servers and OSs. SAN was quickly replaced with Internet Small Computer Systems Interface (ISCSI) allowing access to stored data over an internet connection. We could then forget about the room of computers, and even build them out in the desert.
The Rise Of Hacking
In the last two decades, we have seen these server technologies jump to the cloud, and witnessed several huge data breaches and rampant ransomware. Now with the emerging 5G networks, opportunities for breaches abound, and old tactics of defense are astoundingly obsolete.
But let’s take a lesson from history, what do you think the good old fellas did to protect their RAMAC 350? Lock the doors, maybe put on a password, and have a security detail guarding the building. That’s what we call integrated security, and that’s what will be essential in the future of data protection.